Understand the backbone of internet communication! Learn about five specific network protocols employed by the average consumer each day: (TCP, UDP, HTTPS, SSH, SMTP). We will consider their ports, purposes, vulnerabilities, and (most importantly) how to secure them. Additionally, we will identify how they may combine to work together.
Decoding Network Protocols and Traffic
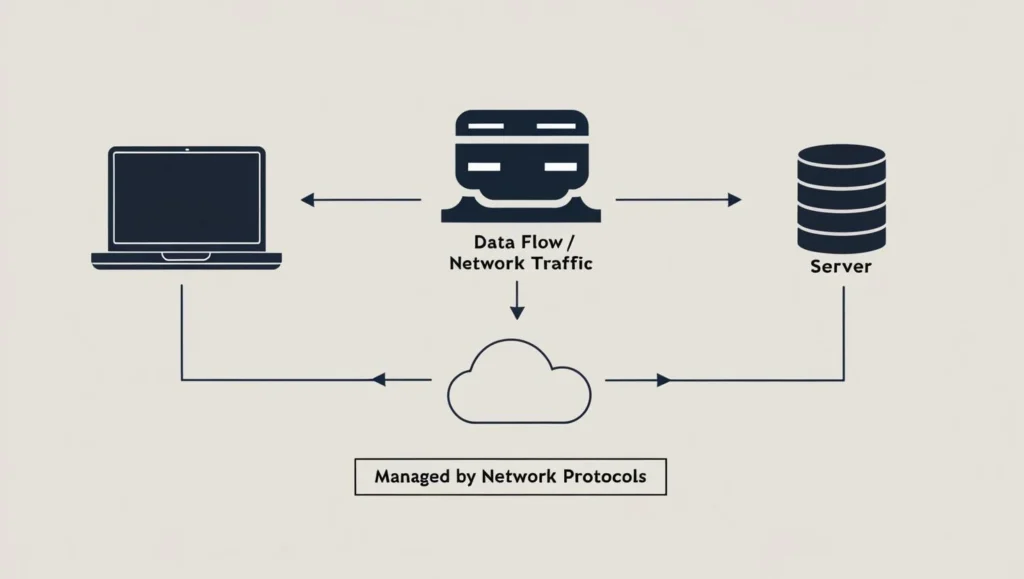
The internet is a vast and complex web of communication, and at its heart lies network protocols. But what exactly is a network protocols, and how does it work? Simply put, network protocols are rules that govern the movement of data between devices on a network. Data flow is made possible by thousands of protocols. Becoming familiar with some of the more common network protocols is fundamental for anyone interested in cybersecurity topics or simply seeking a basic understanding of how the digital world operates.
This article explores five common network protocols and their purposes, features, and potential vulnerabilities. Understanding how these protocols fit into the digital network landscape will empower you to strengthen your home and enterprise network and data security.
5 Common Network Protocols
1. TCP (Transmission Control Protocol): The Reliable Workhorse
- Port: Varies
- Purpose: The TCP network protocol is the cornerstone of reliable data transfer. It ensures that data packets arrive at the correct destination and in order without errors or omissions. This reliability makes TCP essential for applications where data integrity is crucial, such as web browsing and email.
- Features:
- Reliability: TCP establishes a connection before transmitting data, ensuring that every packet is received in sequence. This connection-oriented approach guarantees that lost packets are re-transmitted.
- Ordered Delivery: Data segments are numbered, allowing the receiving device to reassemble them in the correct order. This feature is vital for applications like video streaming, where the sequence of data is crucial for playback.
- Flow Control: TCP regulates data transmission rates to prevent overwhelming the receiver. This is achieved through a mechanism known as windowing, which adjusts data flow based on recipient capacity.
- Vulnerabilities:
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept communication between two parties to steal or manipulate data. This is particularly concerning for sensitive information like passwords and financial data.
- Packet Sniffing: Malicious actors may capture and analyze network packets to extract sensitive information. Popular tools like Wireshark software can be used to detect these types of cybersecurity attacks and secure your network.
- TCP SYN Flood: Attackers might overwhelm a server with connection requests, causing it to become unresponsive to valid requests. This type of denial-of-service attack can disrupt the services of legitimate users.
- Securing TCP: TCP relies on network protocols such as Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), to secure communication over a network.
- Practical application: Your email client (such as Outlook or Gmail) uses the TCP network protocol to ensure that the email message, including attachments, is sent and received reliably and in the correct order. Without TCP, you might experience scrambled words or missing attachments, leading to confusion and miscommunication.
2. UDP (User Datagram Protocol): The Speedy Protocol
- Port: Varies
- Purpose: Unlike TCP, the UDP network protocol prioritizes speed over reliability, making it ideal for applications that require low latency. This is particularly important for real-time applications like gaming and streaming, where delays can significantly impact user experience.
- Features:
- Faster Connection: UDP doesn’t establish a connection before transmitting data, which reduces overhead and improves speed. This makes it suitable for applications where speed is more important than reliability.
- Connectionless: Data packets are sent independently, without regard for order or delivery confirmation. This means packets can arrive out of order or be lost without affecting application performance.
- Vulnerabilities:
- Since UDP does not guarantee delivery, packets may be lost or arrive out of order, potentially leading to data corruption or incomplete transmissions. This can be problematic for applications that require complete data integrity.
- DNS Spoofing: Attackers can manipulate DNS records to redirect users to malicious websites. This can lead to phishing attacks or the distribution of malware.
- UDP Flood Attacks: Attackers can overwhelm a server with UDP packets, similar to a TCP SYN flood, causing it to become unavailable. This type of denial-of-service attack can disrupt services for legitimate users, leading to significant downtime and revenue loss for businesses.
- Securing UDP: To secure UDP communications, it is essential to implement measures such as DNSSEC (Domain Name System Security Extensions) to protect against DNS spoofing. Also, configuring firewalls to filter traffic can help mitigate the risk of UDP flood attacks.
- Practical application: Consider the example of Google Meet. Google recommends utilizing UDP whenever possible because its low latency and high data transfer speed are crucial for real-time video and audio communication. In this context, the speed of UDP allows for smooth conversations without the lag that could disrupt meetings or online classes.
3. HTTPS (Hypertext Transfer Protocol Secure): Secure Web Browsing

- Port: 443
- Purpose: HTTPS is a network protocol that provides a secure and encrypted channel for web browsing, protecting sensitive data from eavesdropping and tampering. It is essential for any website that handles personal information, such as online banking or e-commerce sites.
- Features:
- Encryption: HTTP works together with SSL/TLS encryption protocols to create HTTPS for secure communication between a browser (such as Firefox or Safari) and a web server. This internet protocol encrypts web traffic, ensuring any data exchanged is unreadable to unauthorized parties. This helps prevent phishing attacks where attackers create fake websites to steal user credentials.
- User Authentication: HTTPS verifies the identity of each website by ensuring that visitors are connecting to the legitimate web server. This helps prevent phishing attacks where attackers create fake websites to steal user credentials.
- Data Integrity: HTTPS protects data from being modified during transmission. This means that users can trust that the information they receive is exactly what the server intended to send.
- Vulnerabilities:
- Fraudulent Certificates: Attackers can obtain fake SSL/TLS certificates to impersonate legitimate websites. This can mislead users into thinking they are on a secure site when they are not.
- Vulnerable SSL/TLS Versions: Older versions of SSL/TLS may contain vulnerabilities exploited by hackers. It’s critical to keep these protocols updated to the latest versions to ensure security.
- Man-in-the-Middle Attacks: Although harder, MitM attacks can still be performed on HTTPS connections, especially with compromised certificates. Users should always check for the padlock icon in their browser’s address bar to ensure a secure connection.
- Securing HTTPS: To secure HTTPS web traffic, users should regularly update their devices and browsers, use strong passwords, and be cautious when their browsers warn of insecure connections. Website owners should implement valid SSL/TLS certificates and keep their encryption protocols up-to-date.
- Practical application: If your web browser warns you not to proceed with loading a website, it’s possible your network traffic is about to be directed through the insecure HTTP port 80 rather than the secured HTTPS port 443. Heed the warning and do not proceed! This simple precaution can protect you from potential data breaches and identity theft.
4. DHCP (Dynamic Host Configuration Protocol): Automatic Network Configuration
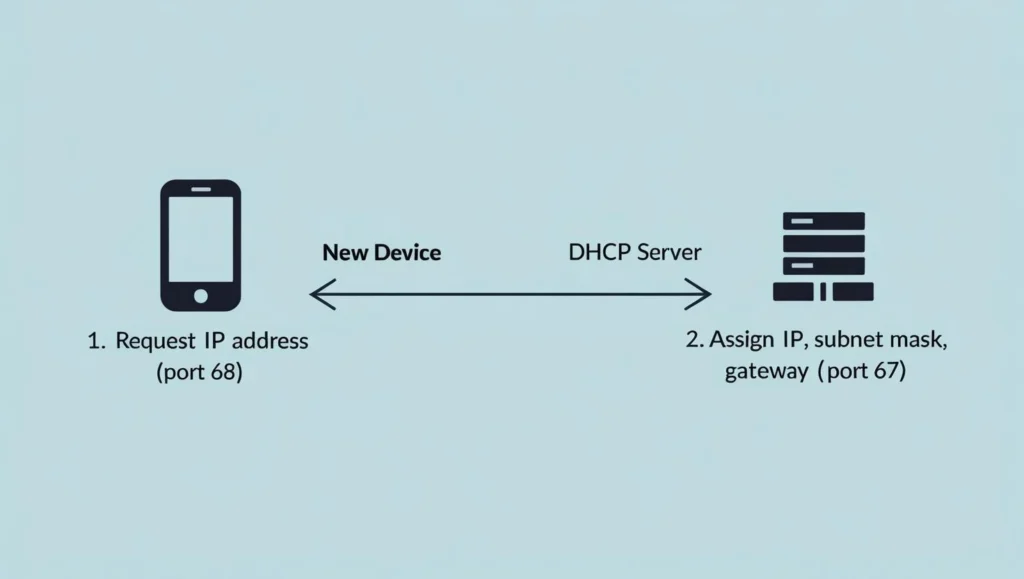
- Port: 67 (DHCP server), 68 (DHCP client)
- Purpose: DHCP is a network protocol that automatically assigns IP addresses, subnet masks, default gateways, and DNS server addresses to devices on a network. This allows devices to connect seamlessly without requiring manual configuration, making it easier for users to access the internet.
- Features:
- Automatic IP Address Assignment: Eliminates the need for manual configuration.
- Dynamic Allocation: IP addresses are leased for a specific period, allowing for the efficient use of available addresses.
- Centralized Management: DHCP servers manage IP address allocation, simplifying network administration.
- Vulnerabilities:
- DHCP Spoofing: Attackers can set up rogue DHCP servers to distribute malicious IP addresses and DNS settings, redirecting traffic to their control. This can lead to data theft or malware infections.
- DHCP Starvation: Attackers can flood the DHCP server with requests, depleting the available IP addresses and preventing legitimate devices from connecting. This can disrupt network services for users.
- Man-in-the-Middle Attacks: If a rogue DHCP server is set up, the attacker can perform man-in-the-middle attacks, intercepting and manipulating data between users and legitimate servers.
- Securing DHCP:
- Implement DHCP snooping on network switches to prevent rogue DHCP servers.
- Use port security to restrict the number of MAC addresses that can connect to a port.
- Monitoring DHCP server logs for suspicious activity can help identify potential threats.
- For critical network devices, implement static IP addresses to reduce reliance on DHCP.
- Practical application:
- Home Networks: Every time a smartphone, laptop, or smart TV connects to a home Wi-Fi network, DHCP is likely assigning it an IP address.
- Public Wi-Fi: When connecting to public Wi-Fi at a coffee shop or airport, DHCP provides the necessary network configuration. This automatic assignment of IP addresses simplifies the user experience, allowing devices to connect to the internet without requiring technical knowledge of network settings.
- Administration: In larger environments, such as corporate offices, DHCP streamlines network management, enabling IT administrators to allocate resources efficiently and maintain connectivity for numerous devices
5. SMTPS (Simple Mail Transfer Protocol Over SSL/TLS): Email Delivery
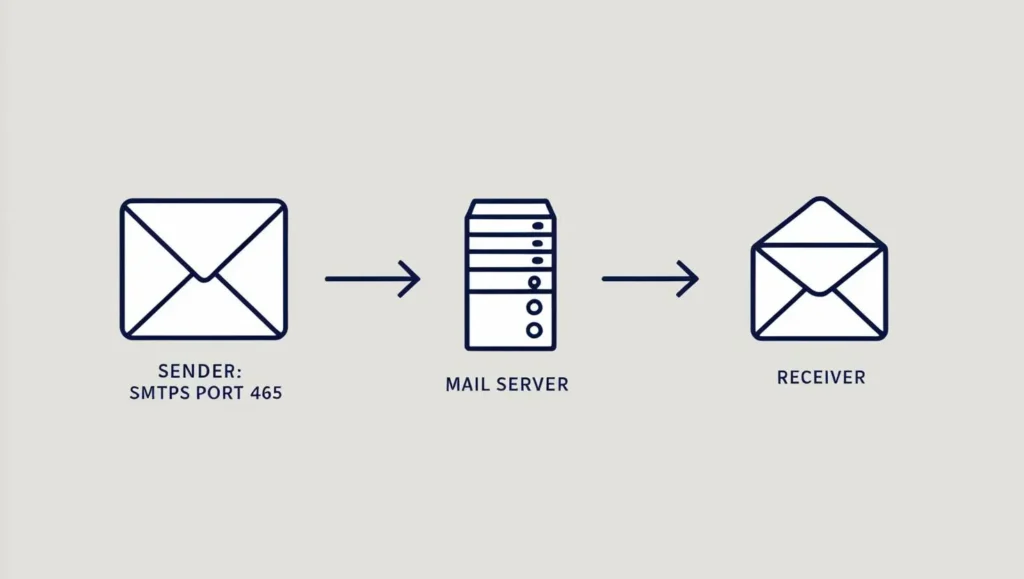
- Port: 465
- Purpose: SMTPS is the network protocol that securely transfers email messages. It is essential for sending emails from clients to servers and between servers themselves, ensuring that messages reach their intended destination.
- Features:
- Email Relay: SMTPS relays email messages from one server to another, facilitating the delivery of messages across the internet. This process involves multiple servers, which work together to ensure emails are delivered promptly.
- Message Delivery: SMTPS ensures email messages are delivered to the intended recipients. If a recipient’s server is unavailable, SMTPS will attempt to resend the message until it is successfully delivered.
- Vulnerabilities:
- Spam: SMTPS is often used to send unsolicited bulk email (spam). This can clutter inboxes and lead to phishing attempts, where attackers try to trick users into revealing sensitive information.
- Phishing: Attackers can use SMTPS to send phishing emails, attempting to trick users into revealing sensitive information. This is a common tactic used in cyberattacks.
- Email Spoofing: Attackers can forge email headers to make it appear like emails are coming from legitimate senders. It leads to trust issues and data breaches when users interact unknowingly with malicious content.
- Securing SMTPS: It is essential to implement measures such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) records. Layering network protocols helps verify the authenticity of email senders and reduces the risk of spam and phishing attacks.
- Practical application: When you send an email, your network traffic flows reliably to its destination with SMTPS. This network protocol ensures that your message is relayed through the necessary servers, reaching the recipient’s inbox efficiently. Understanding how SMTPS works can help users appreciate the importance of email security and the measures needed to protect their communications.
Conclusion
By understanding these fundamental network protocols — TCP, UDP, HTTPS, DHCP, and SMTPS — you can take proactive steps to secure your online environment and protect your valuable data and digital assets. Each protocol plays a crucial role in facilitating communication over the internet but comes with vulnerabilities that can be exploited by malicious actors.
Key Takeaways
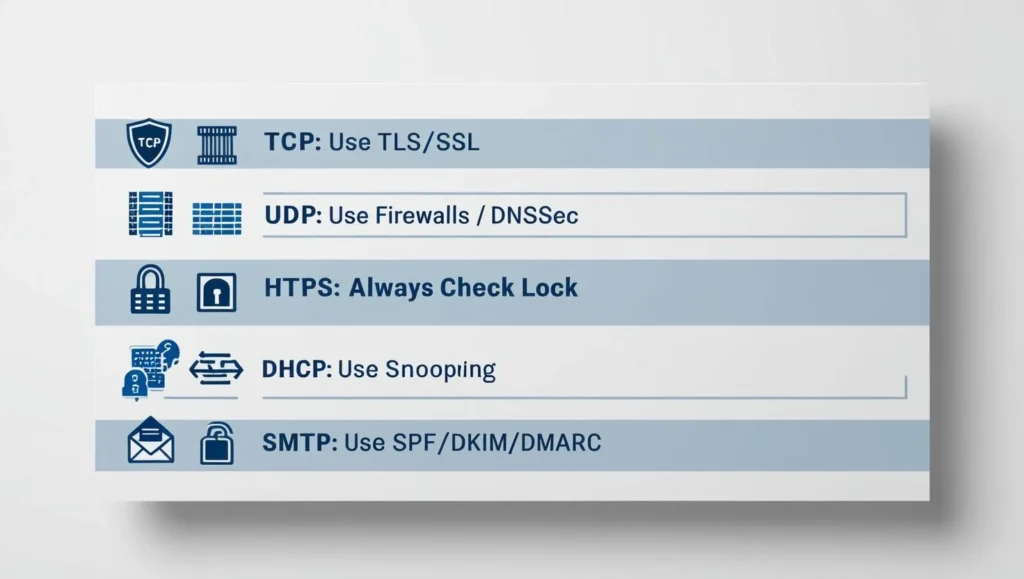
- TCP is essential for reliable data transfer, but it’s vulnerable to MitM attacks and packet sniffing. To secure this network protocol, implementing TLS/SSL is vital.
- UDP prioritizes speed, making it ideal for real-time applications, but it lacks reliability. Implementing DNSSEC and firewalls can help secure UDP traffic.
- HTTPS is vital for secure web browsing, protecting sensitive data from eavesdropping. Users should always look for the padlock icon and ensure their browsers are up to date.
- DHCP simplifies network configurations but is often exploited by spoofing and starvation attacks. Implementing DHCP snooping and monitoring logs can enhance security.
- SMTPS is the backbone of email delivery but is also the target of spam and phishing. Using SPF, DKIM, and DMARC can help secure email communications.
Review Your Network Protocols
Now that you have a foundational understanding of these five essential network protocols, consider reviewing your network security practices. Are you using secure connections when browsing the web? Do you have measures in place to protect your email communications?
By taking these steps, you can safeguard your personal information and contribute to a more secure digital landscape.
To delve deeper into this cybersecurity topic, consider exploring additional resources, such as online courses, WEBINARS, or books on network protocols and security. The more you learn, the better equipped you will be to navigate the complexities of the digital world and protect yourself against evolving cyber threats.